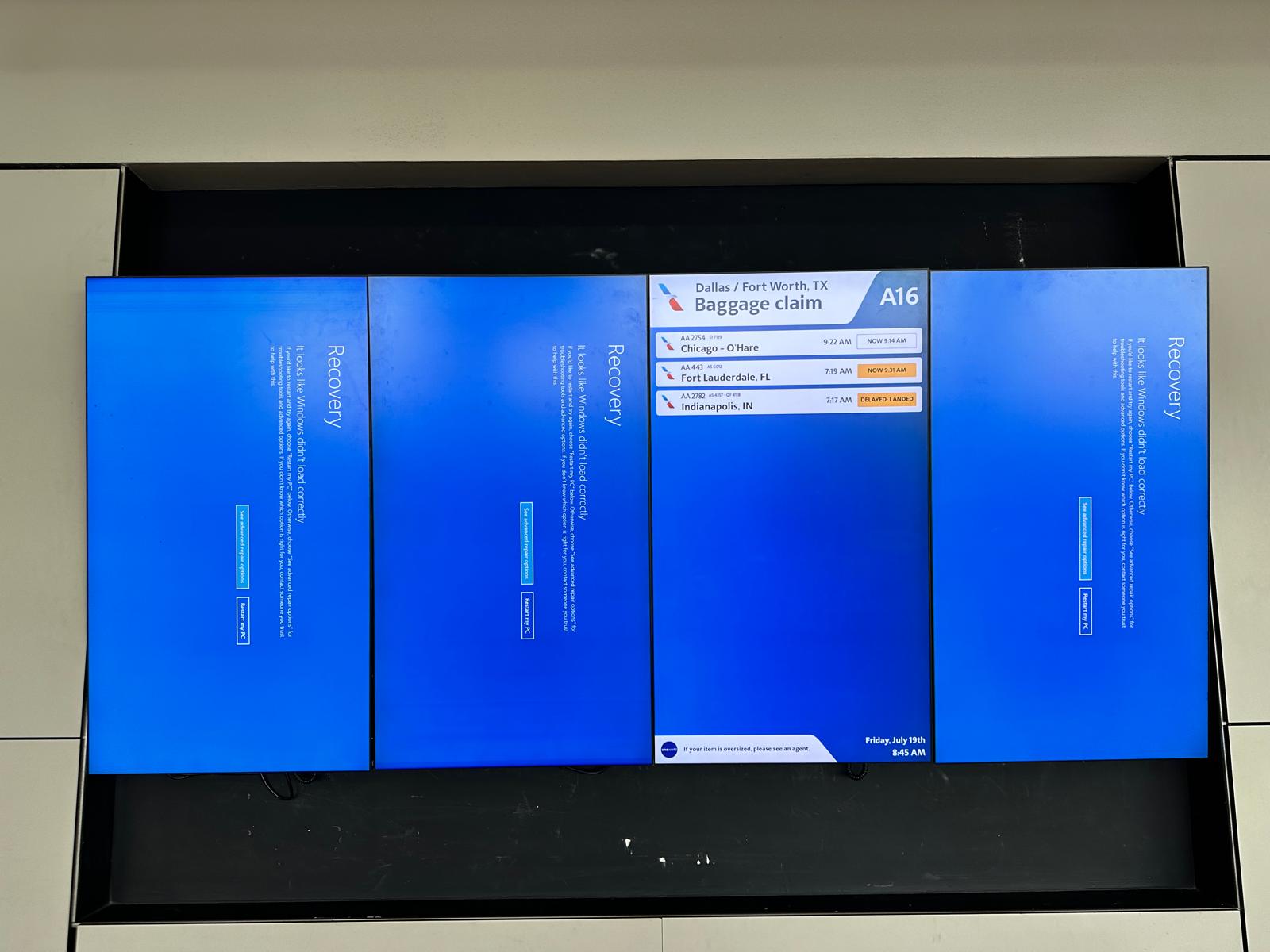
Those in the U.S. hoping for a three-day weekend were in luck last Friday morning. Many around the country like us at FIU awoke to internal emails regarding a "widespread IT issue" facing their institutions. A defect in a software update from CrowdStrike, a leading cybersecurity firm, led to outages for users running Microsoft's Windows operating system. Many users were faced with the dreaded Blue Screen of Death (BSOD) - a notification on the windows operating system stating that "your PC ran into a problem it couldn't handle" and needs to be restarted.
While limited to Windows users, social media speculation ran rampant about who was responsible for the outage. Linux and Mac users used the opportunity to poke fun at the situation as their systems had not been impacted by the update. Florida Senator Rick Scott while ackowledging that Friday's outage appeared not to be caused by a cyber-attack, used the opportunity to call out DHS's Cybersecurity and Infrastructure Agency (CISA) for failing to hold Microsoft accountable for, as the Senator stated, allowing "hacks by foreign actors to jeopardize U.S. national security." Extreme leaning political advocates and conspiracy theorists used the situation to frame loose connections between the outage with what this means for the security of election systems this coming November.
So what really happened? CrowdStrike's Falcon Sensor product, a security tool used to block attacks on systems, released a content update with a defect in one of the channel files leading to Windows users with this update experiencing the BSOD. CrowdStrike president and CEO George Kurtz released a statement soon thereafter ensuring customers that this was not the result of a cyberattack or security incident but rather a defect in the content update for Windows hosts. CrowdStrike then released workaround steps for individual hosts that allowed them to manually locate and remove the defective channel file "C-00000291*.sys" and reboot. CISA released a cybersecurity advisory regarding the incident confirming that the disruption was due to the CrowdStrike Falcon content update and not due to malicious cyber activity. They did, however, observe that threat actors sought to take advantage of this incident for phishing and other malicious activity.
Most customers' systems were partially up and running by lunchtime, but the impact felt by the disruption will have accordion-like effects. Many hospitals in Germany, Israel, and the United Kingdom experienced issues wth their patient records and reservations systems, with some cancelling all non-emergency surgeries until systems were back up. Several news outlets were unable to go live including ABC Australia, Sky News Australia, and Kansas City based KHSB-TV. American Airlines, United Airlines, and Delta Airlines issued ground stops following the incident leading to more than 2,300 flight cancellations and 6,500 flight delays as of this writing. Globally, there have been over 29,000 delays and thousands of cancellations. Global supply chain companies are already bracing for the impact that these delays will cause for customers.
The widespread disruptions caused by CrowdStrike serve as a stark reminder of the vulnerabilities inherent in our rapidly increasing interconnected world. For the U.S., being one of the most connected countries in the world also means that we are among the most vulnerable, and the rapid integration and interdependency of connected systems means that the complexity and breadth of cyber incidents will likely grow more impactful as we move through the 21st century. As global supply chains and their digital infrastructures become more intertwined, the consequences of cyber failures will extend beyond individual organizations and could affect national economies and domestic and national security. The incident also highlights the importance of cybersecurity and IT frameworks such as the National Institute for Standards and Technologies (NIST) Cybersecurity Framework. Expected issues around accountability and responsibility to emerge in the aftermath of Friday's incident, issues not yet clearly defined by national-level policies.
The CrowdStrike incident foreshadows the future challenges of operating in an era of rapidly increasing global interconnectivity. So what can organizations do? Prioritize organizational resilience by fostering a culture of cybersecurity awareness, investing in cutting-edge technologies and capable IT workforces, and developing organizational policies that factor in current and emerging threats and vulnerabilities. Operational continuity will demand that organizations are prepared to both defend against threats and rapidly recover from disruptions - whether dirven by cyber criminals or faulty software updates. Policymakers must also consider efforts that incentivize companies to build greater cyber resilience while also ensuring that organizations that don't prioritize securing systems are held accountable when their customers are impacted. In the end, we must all work together to enhance our collective cyber resilience and ensure that the tradeoffs of greater connectivity favor the benefits and not the risks.
Brian Fonseca is the Director of Florida International University's Jack D. Gordon Institute for Public Policy and Randy Pestana is Director for Cybersecurity Policy at Florida International University's Jack D. Gordon Institute for Public Policy.